Smishing. The term should be familiar to most of us if you’ve taken the latest KnowBe4 cybersecurity training. For those who haven’t finished this quarter’s training, smishing is the distribution of text messages supposedly from a reputable source—such as the CEO—to induce people to reveal personal information or make a payment to someone.
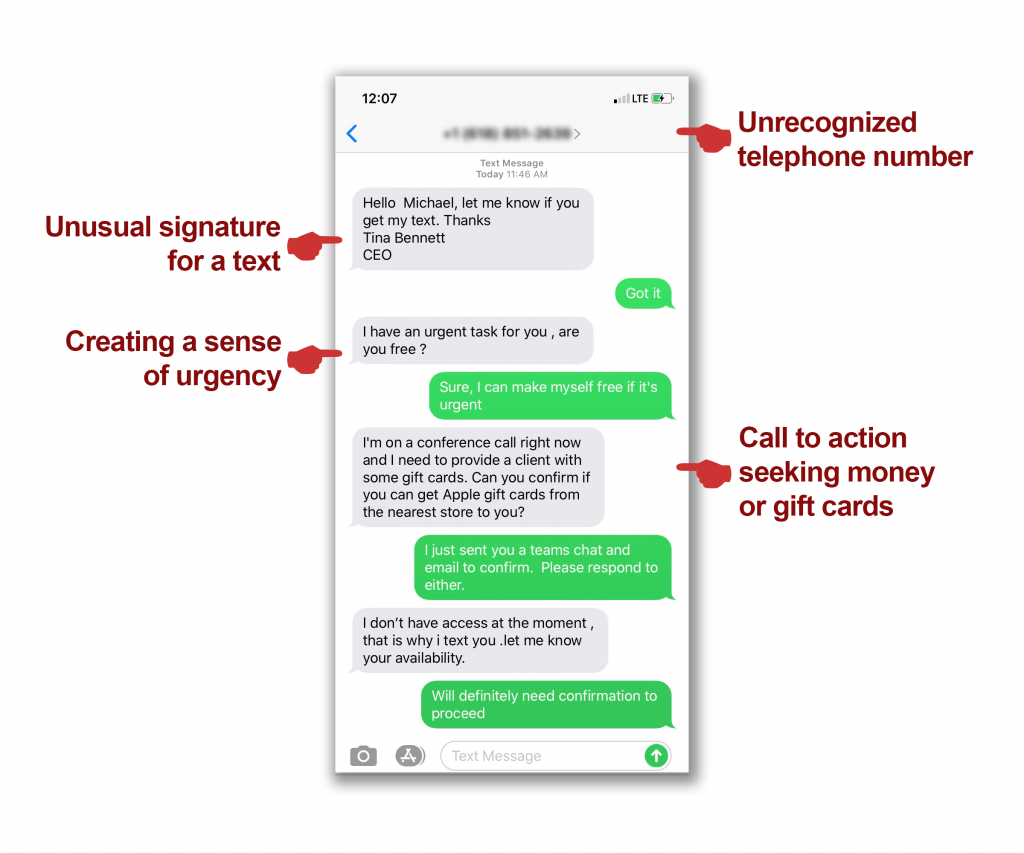
In an unexpected twist, CMC was targeted for a smishing attack last month using Tina Bennett’s name as the “sender.” The attack went to more than 10 employees, including CMC’s CIO Paul Mackay. The employees received a “text” from Tina asking them to pick up some gift cards for her.
As you can see, this smishing attack has several warning signs that our training highlighted. Fortunately, nobody fell for this trick, but it demonstrates the prevalence of cyberattacks and the many ways they can occur.
“CMC employees are our greatest defense against cyberthreats and our greatest weakness,” said Mackay. “With training and vigilance, we can nip these threats in the bud. However, it just takes one hurried moment or carelessly opening an attachment to put CMC’s—or your personal—finances in danger.”
To help CMC employees protect themselves and the company from these threats, we all have been assigned the KnowBe4 Cybersecurity training, including Season 2 of the Inside Man.
“This training was one of the most popular safety lessons we’ve ever done at CMC,” Mackay said, noting several employees praised the training and even joked about a second season of the gripping Inside Man. “The beauty of this training is that it’s so accessible to people. It’s provided in bite-sized chunks and gives people different ways to learn about cybersecurity, methods to identify potential threats and the myriad of approaches these criminals use to attack a company.”
The KnowBe4 training is just one form of defense CMC has introduced to fight cyberattacks and data loss. In June, CMC is rolling out a software program with the PECO Call Center that will limit the accidental release of personally identifiable information (PII). In the background, IT will detect emails that contain PII such as telephone numbers, account numbers and addresses. If an email has that data, the message will be paused to get approval for the message. After testing with the PECO Call Center, the software will be introduced to the rest of CMC.
“This pilot is another layer of CMC’s defenses to prevent the unintended release of PII,” said Mackay, noting that data breeches can lead to fines and hurt CMC’s reputation.
Additionally, CMC has added a button in Outlook near the far right side of the screen to instantly report potential cyberattacks. Just click on it and you can alert IT to possible attacks.
These defensive maneuvers come hot on the heels of Tina Bennett’s “Coffee with Tina” tour, which highlighted a scam that resulted in a substantial theft from CMC.
“Cyberthieves are using increasingly sophisticated methods to try to trick us into providing valuable information or money to them,” Mackay concluded. “This training and the data loss prevention efforts CMC is making can help you avoid these scams at work and teach you vital cyber-self-defense skills.”

